The Identify of CryptoFortress
Another ransomware named CryptoFortress has been discovered in early March, 2015, targeting computers running Windows operating systems. It comes out as a Crypto+ family member.
CryptoLocker, CryptoWall 2.0 and CryptoWall 3 are the previous versions of Crypto+ series. They are all created to encrypt victims files and force them to pay for the randsom money as Bitcoin. Also, a ransome note and deadline are displayed to remind you to deliver the money to them. Though they appear as different names, the essence of them is trojan Teerac.A.
Come to Say ' Hello' to the Crypto+ family members:
The screen shot of CrypLocker ( released on 5 September 2013)
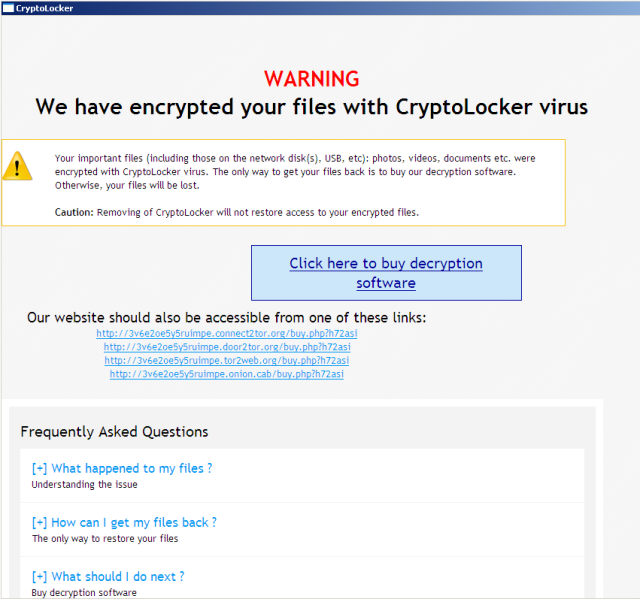
The screen shot of CryptoWall (released in the second half of 2014)
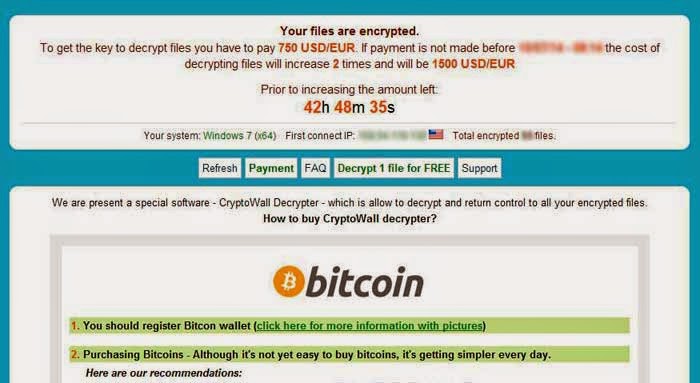
The screen shot of CryptoFortress ( released on March 3, 2015)
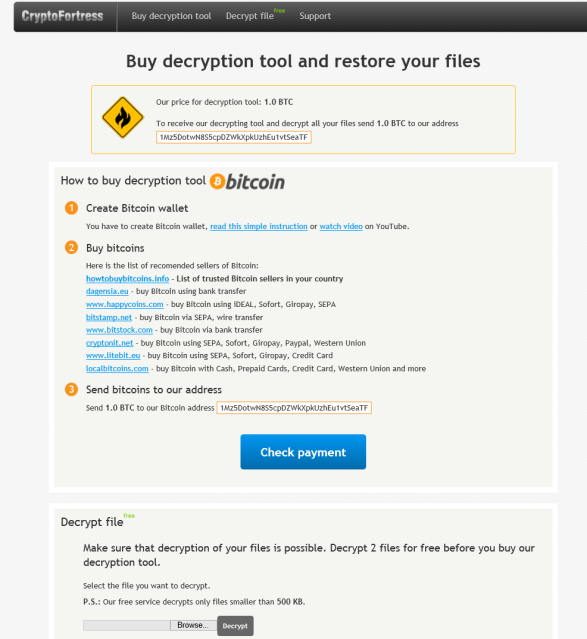
You can see from those annoying ransomware family members, CryptoFortress appears to be a very slightly modified previous Crypto+ members.
How does CryptoFortress get on your PC?
CryptoFortress masquerades itself as a legitimate e-mail attachment. If it is activated , the malware will use RSA public-key cryptography to encrypt files or some files on the Internet with the private key stored only on the malware's control servers.
The worm displays a message indicating that if money is paid before deadlines ( via Bitcoin or other stored value pipeline ) , files will be decrypted. Otherwise the private key will be destroyed , no longer opening these files. If the deadline is not met, the malware will also provide an online service provided by the malicious software controlled decryption. The price of not paying before the deadline is to pay significantly high bitcoins. Before you pay, you need to know that there isn't sure you can get back your files after the payment. You might try to restore the files before you make the decision to pay.
You can try these methods to recover your files.
Procedure 1: download and install the security tool to block CryptoFortress to do encryption again before restoring the files:
1. Click the icon blow to download the powerful removal tool.
(Tip: get into Safe Mode with Networking to download it if your PC performs badly:
Restart your computer >> As your computer restarts but before Windows launches, tap “F8″ key constantly >> Use the arrow keys to highlight the “Safe Mode with Networking” option and then press ENTER >> If you don’t get the Safe Mode with Networking option, please restart the computer again and keep tapping "F8" key immediately.)
2. Click Ctrl+J together to get the all the download files if you are using Google. Search for SpyHunter-Installer.exe. In order to install the removal tool, you need to give your permission by clicking Run.
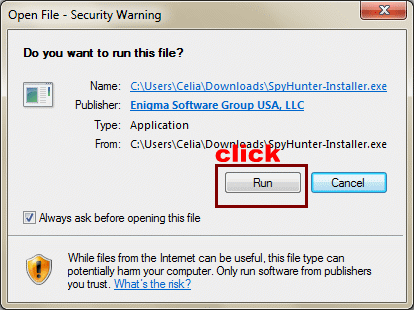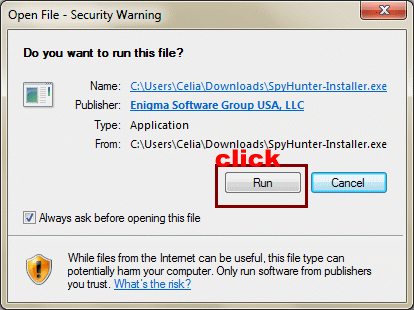
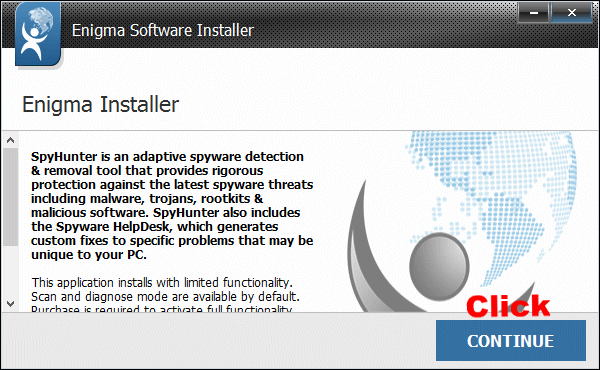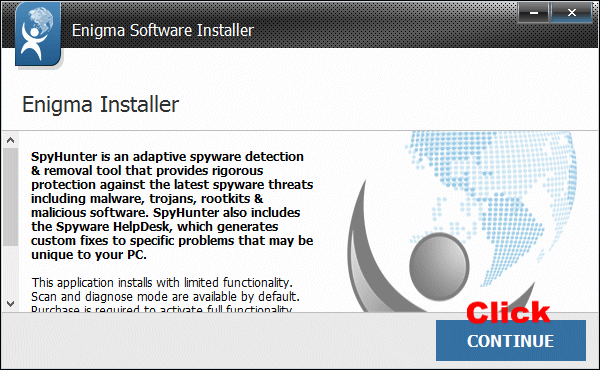
Please follow the pop-up box prompts to accomplish the SpyHunter Installation. Choose Continue to click to get the Install option
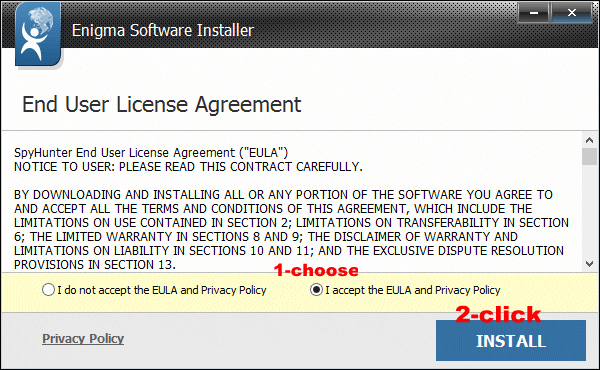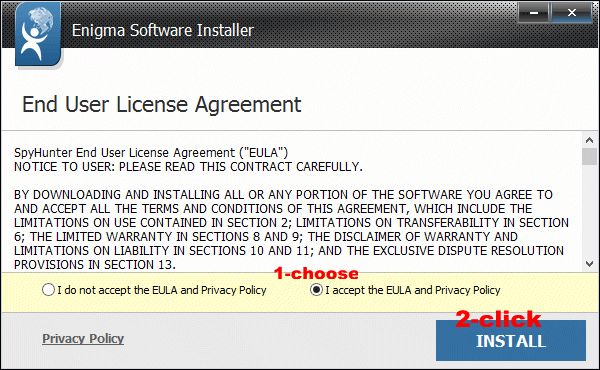
Choose "I accept the EULA and Privacy Policy" and then click INSTALL.
You need to be patient when you are arriving 'downloading file'. It will take a while.
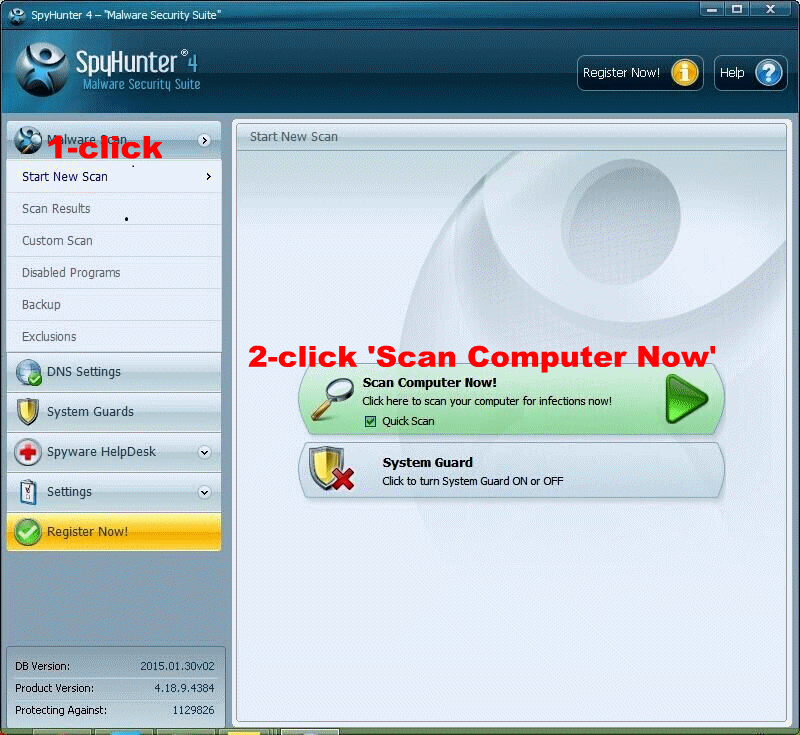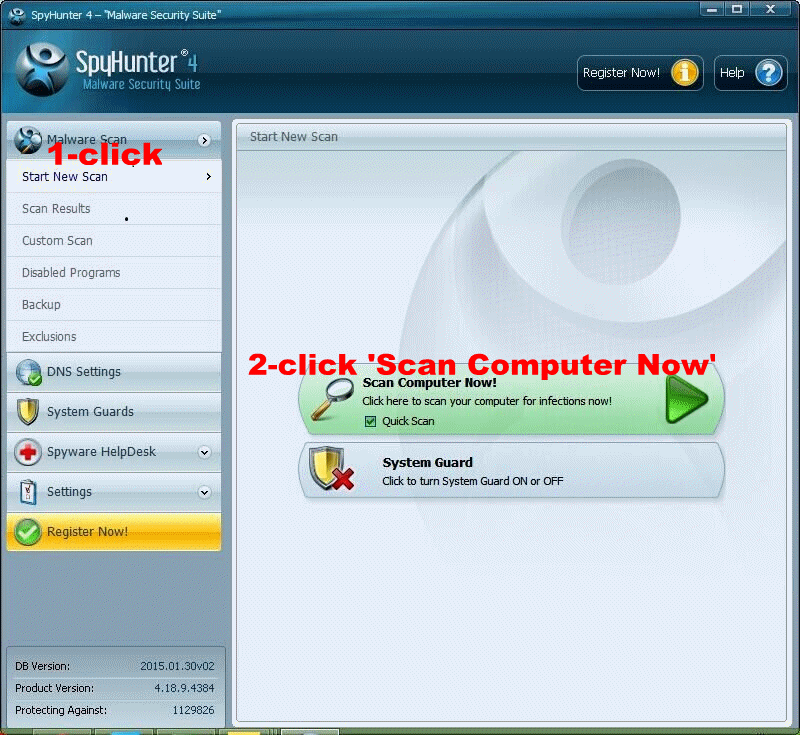
Click Start New Scan to detect and remove all the infected files.
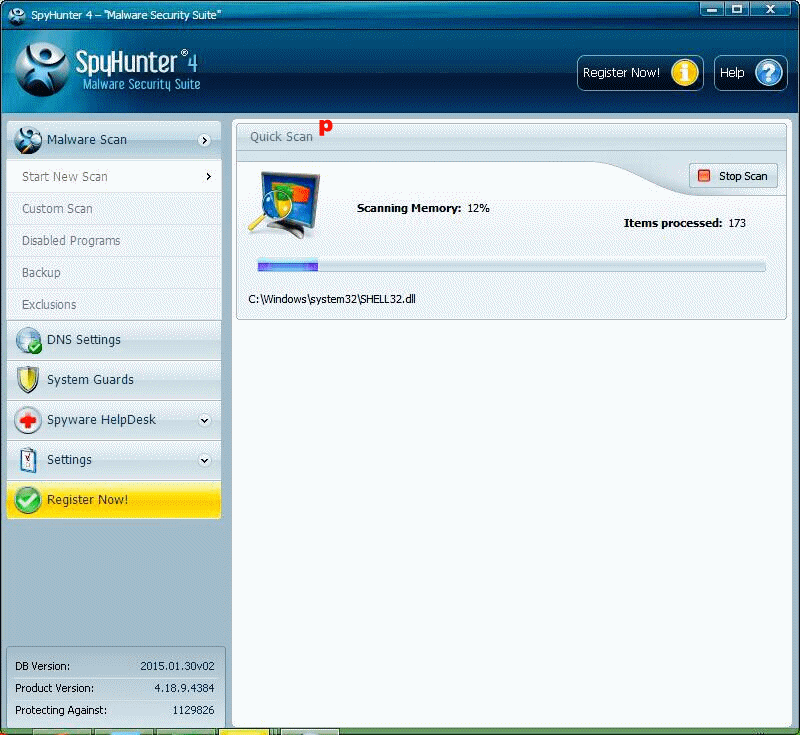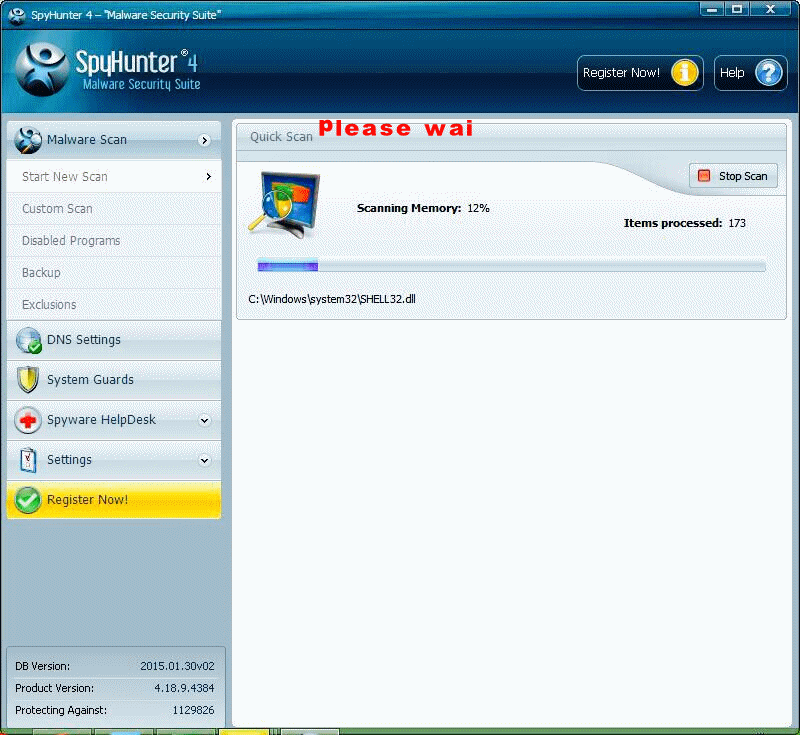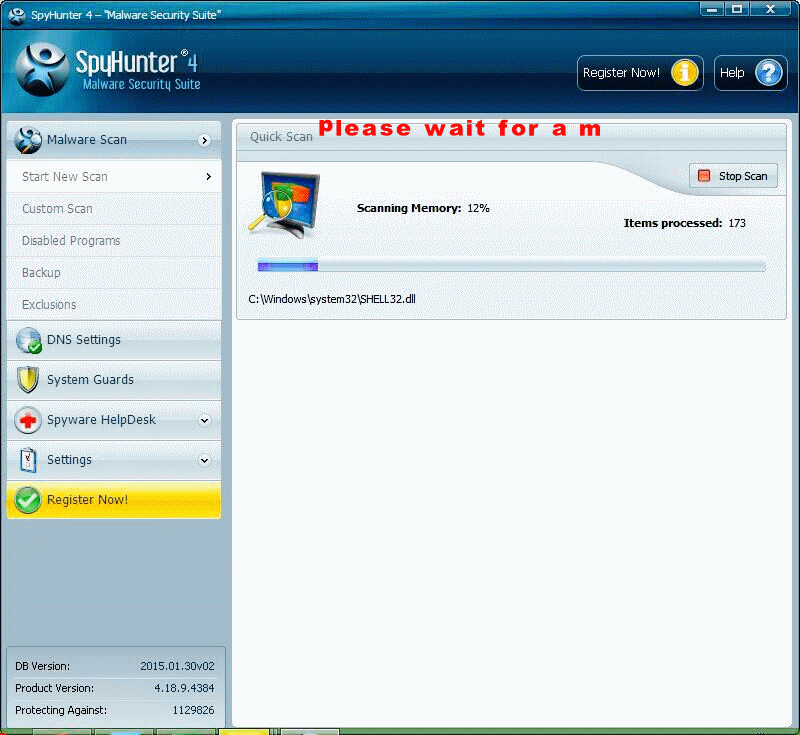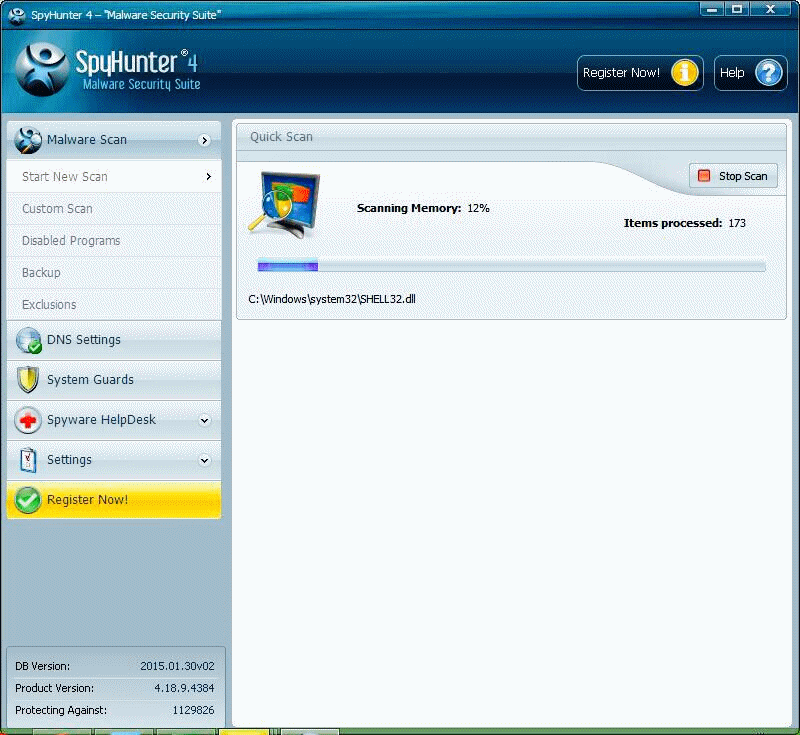
Notice: more than 30 minutes is required to complete the scanning. You are free to standby or go away to have something to drink.
You know what to do: click ' Fix Threats'. You are on the high way to block CryptoFortress.
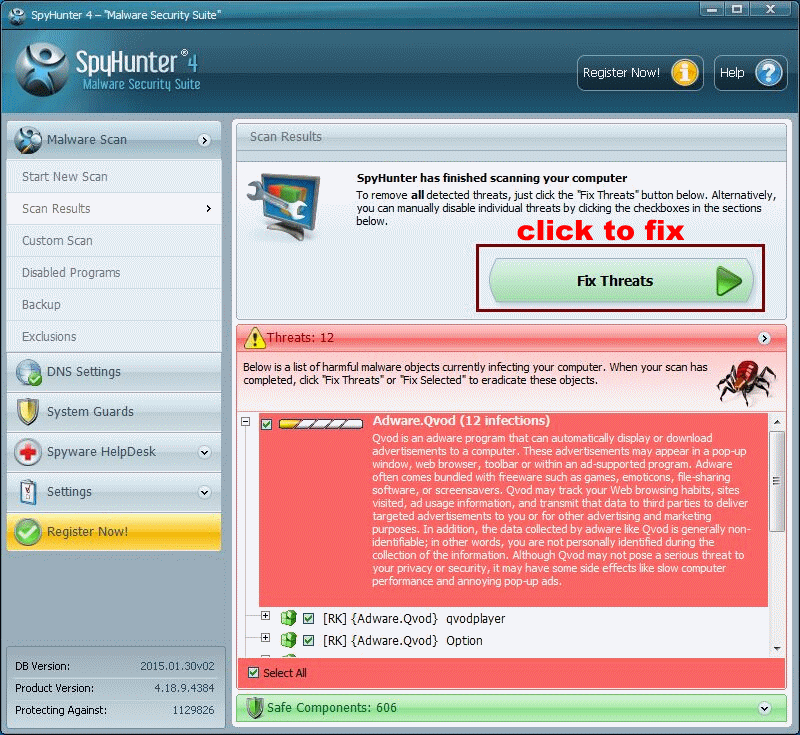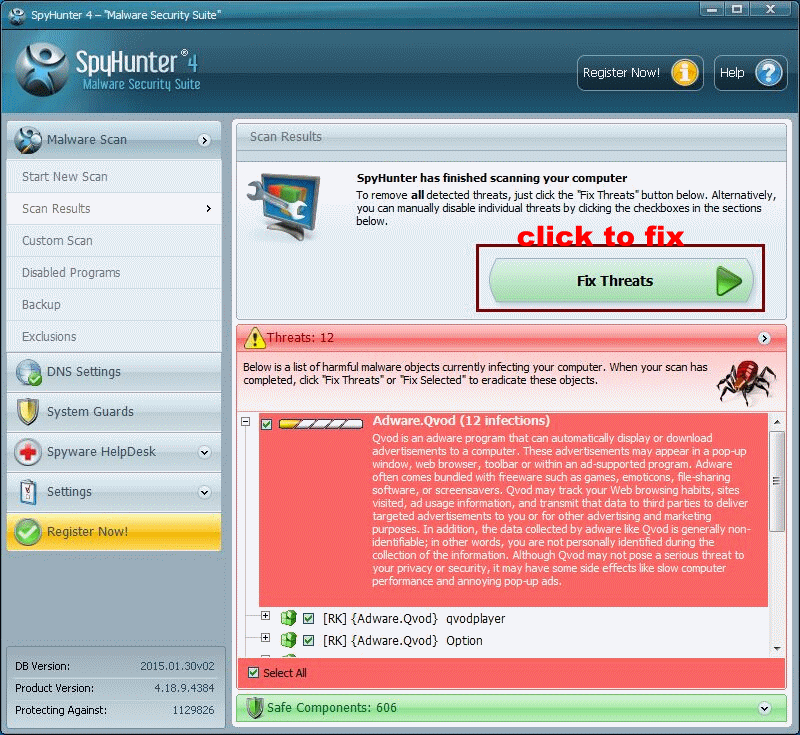
( Tip: If you choose not to block the ransomware, you are possible to lose the opportunity to restore your files.)
Procedure 2: try backups
If you have been performing backups, then it the first and best method to restore your files from a the latest backup.
Procedure 3:try recovery software
Before delete the original files, CryptoFortress makes a copy before it encrypts. Due to this you are able to use the file recovery software like Photorec or R-Studio to possibly get back some of your original files.
Procedure 3: try shadow volume copies
As of now, if CryptoFortress doesn't delete your 'shadow volume copies', it may be a chance to restore your original files from them.
(All in All : don't give up easily. With your trying hard, you may be able to get back some of your fiels. At least try to download the security tool to block CryptoFortress and try the 3 methods to get your files.)

No comments:
Post a Comment
Note: Only a member of this blog may post a comment.